Leaving slide mode.
PCIv4 Implemenatation
westin.wrzesinski@shopify.com
TPAC 2024
Anaheim CA, USA
hybrid meeting
23–27 SEPTEMBER 2024
PCI v4 Synopsis
PCI v4 goes into effect on March 31st 2025. This next major version of PCI adds numerous new controls to protect cardholder data from scripts included on the payment page.
Requirement 6.4.3
| Desciption |
Implementation |
Browser Support |
| Script Authorization |
Content Security Policy (CSP) |
|
| Script Integrity |
Subresource Integrity (SRI) |
|
Requirement 11.6.1
| Desciption |
Implementation |
Browser Support |
|
Detect and respond to unauthorized changes on the Payment Page
including headers and content
|
CSP Reports |
All Major Browsers |
Use Case: Import Maps
Import Maps provide a mechanism to control how the browser resolved
module specifiers when importing JavaScript modules which has many
benefits to anyone using modules in production
Not all browser support integrity metadata set on import maps
Example: Import Maps
<script type="importmap">
{
"imports": {
"emailform": "https://cdn.dev/emailform@1.10.7",
"shippingform": "https://cdn.dev/shippingform@1.10.7"
}
}
</script>
<script type="module">
import emailform from "emailform";
import shippingform from "shippingform";
emailform.render("#contact");
shippingform.render("#shipping");
</script>
Solution: Complete support of SRI in import maps
This feature is not yet supported in all major browsers and was
introduced in June of 2024 so pending browser support strategy may not
be feasible to use import maps with SRI by March 2025
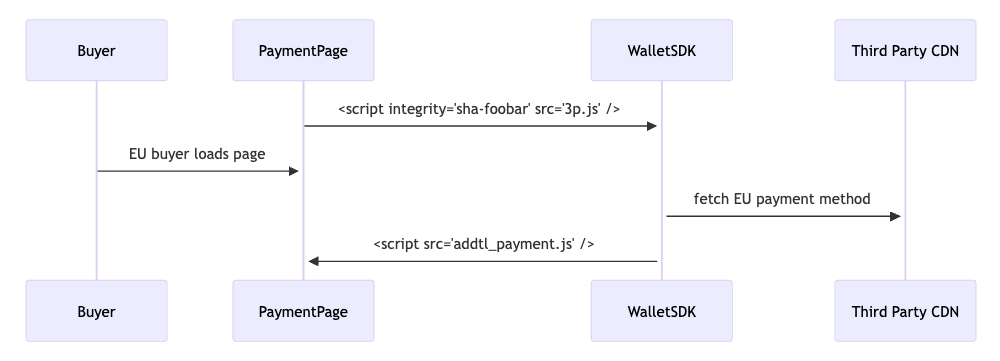
Use Case: Dynamic Subresources
 No browser support to require SRI
No browser support to require SRI
Potential Solution: Revive require-sri-for
require-sri-for is currently not active or supported but
would allow enforcement of SRI prescense on script assets throughout the
page lifecycle
Use Case: Third Party Evergreen SDKs
Payment Pages rely on Wallet or Pixel pages from third party vendors.
Many of the most popular of which are evergreen versioned. This allows
patches to be applied without coordination. This however will not play
nice with SRI.
SRI can not be provided or requires complex coordination
Potential Solutions: Third Party Evergreen SDKs
- Sandbox in iFrames
-
Request vendors to versions assets and coordinate with consumers for
updates
Represent architectural changes, inability to implement quick
patches, and complex cordination
Open Questions
- Will vendors rearchitect with static versions for SRI?
-
How can vendors coordinate release of SRI securely across
consumers?
- When will all major browsers support SRI in import maps?
- Will
require-sri-for be adopted before March 2025?
 No browser support to require SRI
No browser support to require SRI
Introduction